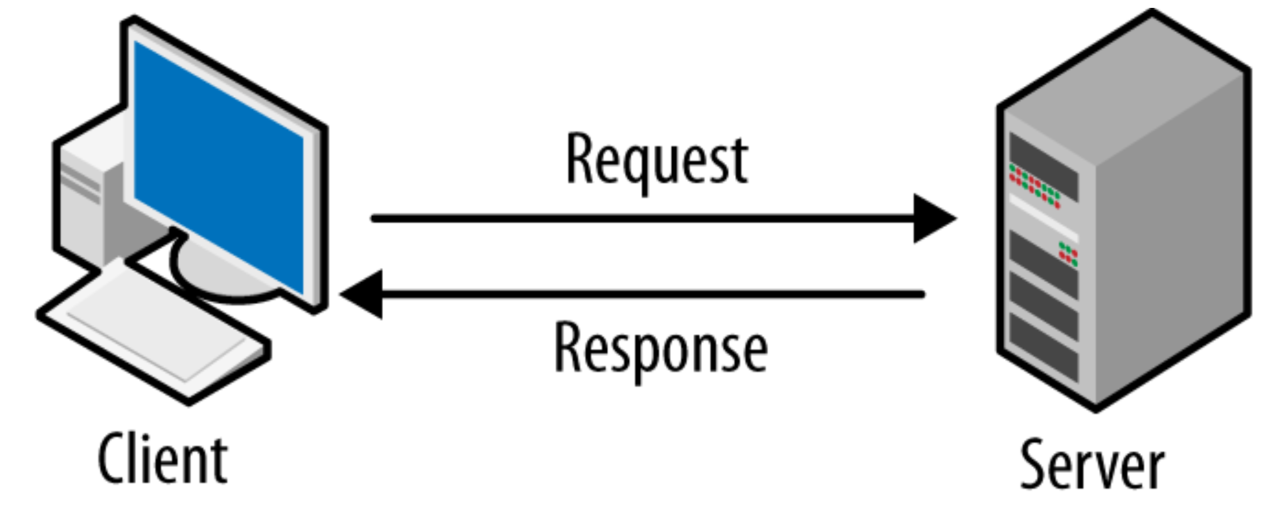
Client server – Client-server architecture sets the stage for a fundamental understanding of how modern applications function. It describes the interplay between two distinct entities: clients, which are devices or programs requesting services, and servers, which provide those services. This dynamic duo, working in harmony, powers a vast array of applications we encounter daily, from browsing the web to accessing online banking.
Imagine a bustling restaurant. Clients, the hungry patrons, place their orders (requests) to the servers, who process the requests and deliver the desired dishes (data). This analogy highlights the core principles of client-server architecture. Clients initiate communication, servers respond, and data flows between them. This fundamental model forms the backbone of countless applications, enabling seamless communication and data exchange.
Client-Server Architecture
Client-server architecture is a prevalent model in computer networks, defining the relationship between two entities: a client and a server. This architecture is based on the principle of request-response, where a client initiates a request for a service, and the server responds to that request. This model forms the foundation for numerous applications we use daily.
Roles and Responsibilities
The roles and responsibilities of clients and servers are distinct and crucial for the functioning of this architecture.
- Client: Clients are the entities that initiate requests for services. They are typically user interfaces, applications, or devices that interact with the server. Examples include web browsers, email clients, and mobile apps. Clients are responsible for sending requests to the server and receiving responses.
- Server: Servers are responsible for providing services to clients. They are powerful computers that manage resources and data. Servers handle requests from clients, process them, and send back responses. Examples include web servers, database servers, and email servers.
Common Client-Server Applications
The client-server model is widely used in various applications.
- Web Browsing: When you visit a website, your web browser acts as the client, sending a request to the web server hosting the website. The web server processes the request and sends back the website’s HTML code, which your browser displays.
- Email: When you send an email, your email client acts as the client, sending the email to the email server. The email server then forwards the email to the recipient’s email server, where it is stored until the recipient retrieves it.
- Online Banking: When you access your online bank account, your web browser acts as the client, sending requests to the bank’s server. The bank’s server authenticates your identity and provides access to your account information.
- File Sharing: When you share files over a network, your computer acts as the client, sending the files to the server. The server stores the files and makes them available to other clients who request them.
Communication Protocols: Client Server
Client-server systems rely on communication protocols to establish and maintain connections between clients and servers. These protocols define the rules and formats for exchanging data, ensuring that both parties understand the information being transmitted.
HTTP
HTTP (Hypertext Transfer Protocol) is a widely used protocol for transferring files, especially web pages, across the internet. It is a request-response protocol, where a client sends a request to a server, and the server responds with the requested data.
Characteristics of HTTP
- Stateless: Each request is treated independently, without any knowledge of previous interactions.
- Text-based: HTTP uses plain text for communication, making it human-readable.
- Flexible: HTTP supports various methods, such as GET, POST, PUT, and DELETE, for different types of requests.
Applications of HTTP
- Web browsing: HTTP is the foundation of the World Wide Web, enabling users to access and view web pages.
- API communication: HTTP is commonly used for building and accessing APIs, allowing different applications to interact with each other.
- Data transfer: HTTP can be used to transfer various types of data, including text, images, videos, and files.
TCP/IP
TCP/IP (Transmission Control Protocol/Internet Protocol) is a suite of protocols that forms the foundation of the internet. TCP provides reliable, ordered delivery of data, while IP handles the addressing and routing of data packets.
Characteristics of TCP/IP
- Connection-oriented: TCP establishes a connection between the client and server before data transmission, ensuring reliable delivery.
- Ordered delivery: TCP guarantees that data packets arrive in the correct sequence, even if they are transmitted out of order.
- Error checking: TCP includes mechanisms for detecting and correcting errors during transmission.
Applications of TCP/IP
- Internet communication: TCP/IP is the backbone of the internet, enabling communication between computers worldwide.
- Network services: Many network services, such as email, file transfer, and web browsing, rely on TCP/IP.
- Local area networks: TCP/IP is also used in local area networks (LANs) to connect devices within a smaller geographical area.
UDP
UDP (User Datagram Protocol) is a connectionless protocol that provides a simpler and faster way to transmit data. Unlike TCP, UDP does not guarantee reliable delivery or ordered arrival of packets.
Characteristics of UDP
- Connectionless: UDP does not require a connection to be established before data transmission.
- Unordered delivery: UDP packets may arrive out of order or may be lost during transmission.
- Lightweight: UDP has lower overhead than TCP, making it suitable for applications that prioritize speed over reliability.
Applications of UDP
- Streaming media: UDP is often used for streaming media, such as video and audio, where slight delays are acceptable.
- Online gaming: UDP is commonly used in online games to minimize latency and ensure a responsive gaming experience.
- DNS queries: UDP is used for Domain Name System (DNS) queries, which are typically short and require fast responses.
Network Sockets
Network sockets are endpoints for communication between processes on different machines. They provide a way for applications to send and receive data over a network. In client-server systems, the client creates a socket to connect to the server’s socket.
Role of Network Sockets
- Connection establishment: Sockets are used to establish and maintain connections between clients and servers.
- Data transmission: Data is sent and received through sockets, allowing for communication between applications.
- Address binding: Sockets are bound to specific IP addresses and ports, enabling applications to identify and communicate with each other.
Types of Network Sockets
- Stream sockets: Provide reliable, ordered delivery of data, similar to TCP.
- Datagram sockets: Offer faster, connectionless communication, similar to UDP.
Server Types
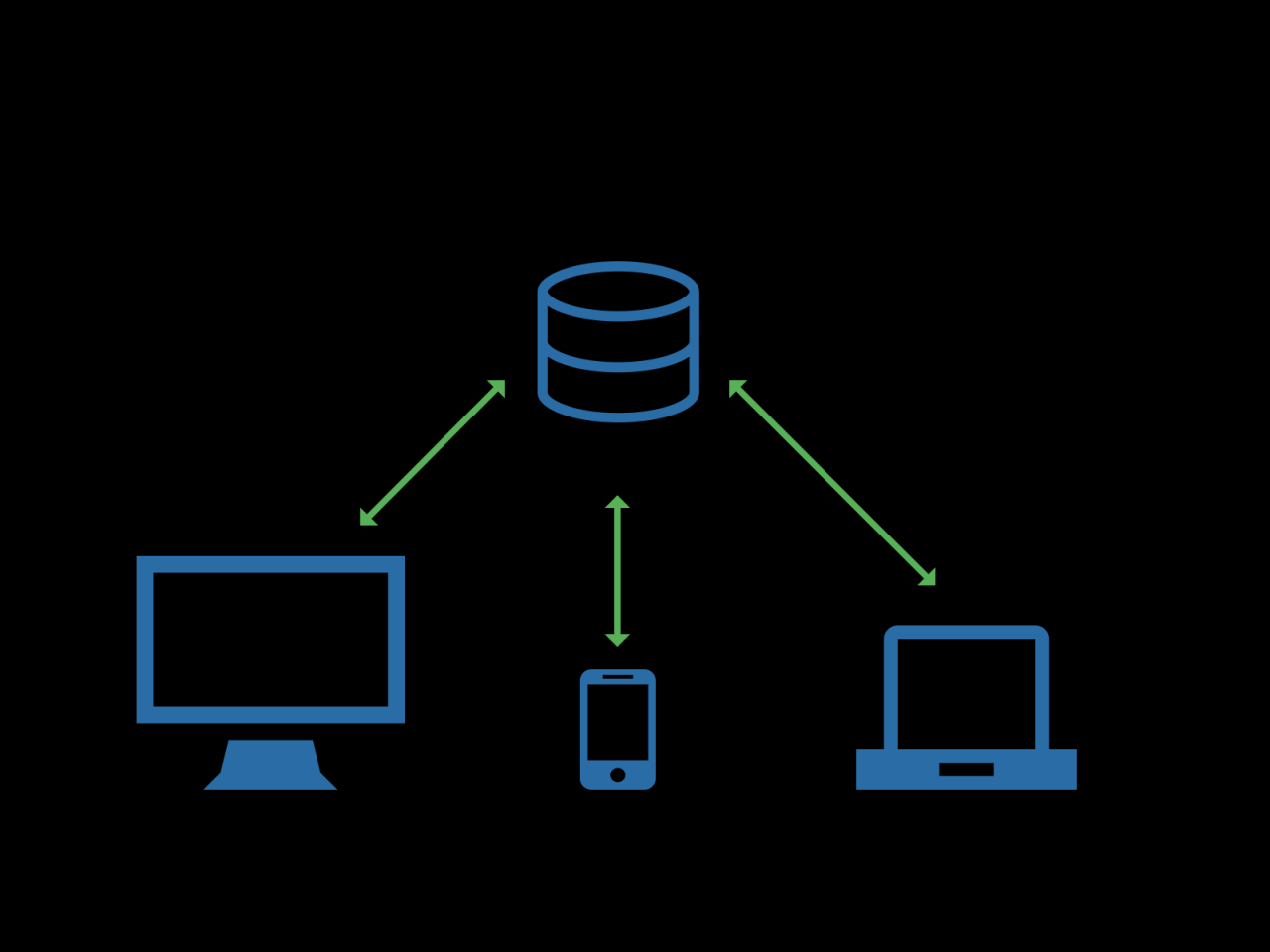
Servers are the backbone of any network, providing essential services and resources to clients. They are categorized based on their specific functionalities and roles within a network.
Web Servers
Web servers are responsible for delivering web pages and other web content to users. They handle requests from clients, process them, and send back the requested information. Popular web server software includes Apache, Nginx, and Microsoft IIS.
- They process HTTP requests from clients, retrieve the requested files from the server’s file system, and send them back to the client.
- Web servers can also serve dynamic content, such as web applications, by interacting with other software components like databases or application servers.
- They are responsible for managing user authentication, session management, and security measures to protect the web server and its content.
Database Servers
Database servers store and manage large amounts of data, providing access to this data for various applications and users. They are responsible for data storage, retrieval, and manipulation. Popular database management systems include MySQL, PostgreSQL, Oracle Database, and Microsoft SQL Server.
- They manage data storage and organization, ensuring data integrity and consistency.
- Database servers handle queries from applications and users, retrieving and manipulating data according to specific requests.
- They enforce security measures to protect sensitive data from unauthorized access and manipulation.
Application Servers
Application servers provide a runtime environment for web applications and other software applications. They handle the execution of application logic, manage resources, and interact with other software components. Popular application server software includes Tomcat, JBoss, and WebSphere.
- Application servers manage the execution of application code, providing a platform for web applications to run.
- They handle requests from clients, process them according to the application’s logic, and send back responses.
- Application servers manage resources, such as memory and threads, to ensure efficient application performance.
Server Types Summary, Client server
| Server Type | Role | Protocols | Common Applications |
|---|---|---|---|
| Web Server | Delivering web pages and content | HTTP, HTTPS | Websites, web applications, REST APIs |
| Database Server | Storing and managing data | SQL, NoSQL | Databases, data warehousing, analytics |
| Application Server | Running web applications and other software | HTTP, HTTPS, SOAP, REST | Web applications, enterprise applications, mobile apps |
Client-Side Technologies
Client-side technologies are the software applications and tools that users interact with directly to access and utilize services provided by servers. These technologies form the bridge between users and the server-side infrastructure, enabling a seamless and interactive user experience.
Web Browsers
Web browsers are the primary client-side technology for accessing and interacting with web-based applications. They are software applications designed to interpret and display web pages, allowing users to browse the internet, access online services, and engage with dynamic content.
- HTML, CSS, and JavaScript: Web browsers utilize these core web technologies to render web pages, style their presentation, and add interactive functionality.
- HTTP Protocol: Browsers communicate with servers using the HTTP protocol, sending requests for web pages and receiving responses containing HTML, CSS, and JavaScript code.
- Rendering Engine: Browsers use rendering engines to interpret the received HTML, CSS, and JavaScript code and transform them into the visually displayed web page.
Mobile Apps
Mobile applications are software programs designed for mobile devices, such as smartphones and tablets. They provide users with a platform to access services and functionalities tailored to their mobile environment.
- Native Apps: These apps are developed specifically for a particular mobile operating system, such as iOS or Android. They offer optimal performance and access to device functionalities but require separate development for each platform.
- Hybrid Apps: These apps combine elements of native apps with web technologies, using web views to display content and interact with the device. They offer a balance between platform compatibility and performance.
- Cross-Platform Frameworks: Frameworks like React Native, Flutter, and Xamarin allow developers to create apps that can run on multiple platforms with a single codebase, reducing development time and effort.
Desktop Applications
Desktop applications are software programs designed to run on personal computers, offering a wide range of functionalities for various tasks, including productivity, entertainment, and specialized operations.
- GUI (Graphical User Interface): Desktop applications typically utilize a graphical user interface (GUI) to provide users with an intuitive and visually appealing way to interact with the software.
- Local Storage: Desktop applications often utilize local storage on the user’s computer to store data, settings, and files, enabling offline access and persistence.
- Client-Server Communication: Many desktop applications communicate with servers to access data, update functionalities, and synchronize information across multiple devices.
Client-Side Frameworks and Libraries
Client-side frameworks and libraries play a crucial role in simplifying client-server communication and enhancing user experience. These tools provide developers with pre-built components, functionalities, and patterns that streamline the development process.
- React: A JavaScript library for building user interfaces, React enables efficient rendering and component-based development, facilitating the creation of dynamic and interactive web applications.
- Angular: A comprehensive JavaScript framework for building web applications, Angular provides a structured approach with data binding, routing, and other features, enhancing development efficiency and maintainability.
- Vue.js: A progressive JavaScript framework, Vue.js offers a flexible and lightweight approach to building user interfaces, making it suitable for both small and large-scale projects.
Data Transfer and Processing
In a client-server architecture, data transfer is the backbone of communication between clients and servers. It involves the exchange of information, enabling clients to request services and servers to respond with the requested data. This process involves several aspects, including the methods used for data transmission, the formats in which data is encoded, and how servers handle client requests.
Data Transfer Methods
Data transfer between clients and servers typically happens over a network using various protocols, such as HTTP (Hypertext Transfer Protocol) or FTP (File Transfer Protocol). These protocols define the rules for exchanging data, ensuring seamless communication between different systems.
- HTTP: The most common protocol for web-based applications, HTTP is used for transferring web pages, images, and other resources between web servers and web browsers. It uses a request-response model, where clients send requests to servers, and servers respond with the requested data.
- FTP: Designed for transferring files between computers, FTP allows clients to upload and download files to and from servers. It uses a separate control connection for commands and a data connection for transferring the actual files.
Data Formats
Data exchanged between clients and servers needs to be structured in a way that both parties can understand. Different data formats have emerged to address this need, each with its strengths and weaknesses.
- JSON (JavaScript Object Notation): A lightweight and human-readable format, JSON is widely used for data exchange in web applications. It uses a simple syntax based on key-value pairs, making it easy to parse and manipulate data.
- XML (Extensible Markup Language): A more structured and extensible format than JSON, XML uses tags to define data elements and their relationships. It is often used for complex data structures and data sharing between different systems.
- HTML (Hypertext Markup Language): The standard language for creating web pages, HTML is used to structure and display content on the web. While primarily used for content presentation, it can also be used to transfer data between clients and servers.
Server-Side Processing
When a client sends a request to a server, the server processes the request and generates a response. This processing involves several steps:
- Request Reception: The server receives the client request, including the requested resource, method (GET, POST, etc.), and any additional data.
- Request Interpretation: The server interprets the request to determine the desired action and the required data. It might involve accessing databases, executing scripts, or retrieving files.
- Response Generation: Based on the processed request, the server generates a response, which can include data, error messages, or status codes. The response is formatted in a suitable data format, such as JSON or XML.
- Response Transmission: The server sends the response back to the client, completing the request-response cycle.
Security Considerations
Client-server systems, while offering numerous benefits, are also susceptible to various security threats that can compromise data integrity, system availability, and user privacy. Understanding these threats and implementing appropriate security measures is crucial for building robust and secure client-server applications.
Common Security Threats
Client-server systems face a range of security threats, including:
- Unauthorized Access: This occurs when unauthorized individuals gain access to sensitive data or system resources. This can be achieved through various methods, such as exploiting vulnerabilities in software, using stolen credentials, or social engineering tactics.
- Data Breaches: These involve the unauthorized disclosure or theft of confidential information stored or processed by the system. Data breaches can result from various factors, including weak security measures, insider threats, or malicious attacks.
- Denial-of-Service (DoS) Attacks: These attacks aim to disrupt or disable the availability of the server or its services by overwhelming it with excessive traffic or requests. This can make the system unresponsive to legitimate users, impacting its performance and accessibility.
Security Measures
To mitigate these threats, security measures must be implemented on both the client and server sides:
Client-Side Security Measures
- Secure Client Software: Using secure and up-to-date software, including operating systems, web browsers, and applications, helps prevent vulnerabilities that attackers can exploit. Regular software updates are essential to patch known security flaws.
- Strong Passwords and Multi-Factor Authentication (MFA): Employing strong passwords, which are long, complex, and unique for each account, significantly reduces the risk of unauthorized access. MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code, making it harder for attackers to gain access.
- Antivirus and Malware Protection: Installing and maintaining antivirus software on client devices helps detect and remove malicious software that can steal data, compromise system security, or launch attacks.
- Firewall: Firewalls act as a barrier between the client device and the network, filtering incoming and outgoing traffic based on predefined rules. They help prevent unauthorized access and malicious attacks.
Server-Side Security Measures
- Secure Operating System and Software: Implementing a secure operating system and regularly updating server software is essential to patch vulnerabilities and reduce the risk of attacks.
- Strong Access Control: Implementing robust access control mechanisms, such as role-based access control (RBAC), ensures that only authorized users can access specific data and resources.
- Data Encryption: Encrypting sensitive data both at rest and in transit protects it from unauthorized access even if the system is compromised. Encryption algorithms like AES (Advanced Encryption Standard) are widely used for their strong security.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity and take actions to block or mitigate potential attacks.
- Regular Security Audits: Conducting regular security audits helps identify vulnerabilities and weaknesses in the system, allowing for timely remediation.
Security Mechanisms
Here’s a table outlining different security mechanisms and their corresponding benefits and limitations:
| Security Mechanism | Benefits | Limitations |
|---|---|---|
| Encryption | Protects data confidentiality by making it unreadable without the decryption key. | Can be computationally expensive and complex to implement. |
| Digital Signatures | Provides authentication and integrity verification, ensuring the origin and authenticity of data. | Requires a trusted third party for key management and certificate issuance. |
| Firewalls | Control network traffic and block unauthorized access. | Can be bypassed by sophisticated attackers who exploit vulnerabilities or use alternative communication channels. |
| Intrusion Detection Systems (IDS) | Detect malicious activity and alert administrators. | May generate false positives and require careful configuration to avoid excessive alerts. |
| Intrusion Prevention Systems (IPS) | Block malicious traffic and prevent attacks from reaching the system. | Can sometimes block legitimate traffic if not properly configured. |
Advantages and Disadvantages
Client-server architecture, a ubiquitous approach in software development, offers numerous advantages and disadvantages. This section explores the trade-offs involved in choosing this architecture, considering its strengths and limitations.
Advantages
Client-server architecture offers several advantages, making it a suitable choice for many applications:
- Centralized Data Management: Data is stored and managed centrally on the server, ensuring consistency and reducing data redundancy. This simplifies data access and updates, as clients interact with a single source of truth.
- Scalability: Client-server architectures can easily scale to accommodate increasing user demands. By adding more powerful servers or distributing the workload across multiple servers, systems can handle a growing number of clients and data requests.
- Security: Centralized security measures can be implemented on the server, protecting data and resources from unauthorized access. This includes firewalls, access control lists, and encryption protocols.
- Cost-Effectiveness: Client-server architectures can be cost-effective, particularly for large organizations. By sharing resources and software licenses, the overall cost of ownership can be reduced.
- Flexibility: Client-server architectures offer flexibility in terms of platform and device compatibility. Clients can access the server from various devices, including desktops, laptops, and mobile phones.
- Easy Maintenance: Updates and upgrades can be deployed centrally on the server, simplifying maintenance and reducing downtime for clients.
Disadvantages
While client-server architecture offers numerous benefits, it also presents some challenges:
- Single Point of Failure: If the server fails, all clients lose access to the resources and data. This can lead to significant downtime and disruption to business operations.
- Network Dependency: Client-server architectures heavily rely on a stable network connection. Network issues can cause delays, errors, and disruptions in client access.
- Performance Bottlenecks: If the server is overloaded with requests, performance can degrade, leading to slow response times and user frustration. This can be a challenge, especially for applications with a large number of concurrent users.
- Complexity: Implementing and maintaining a client-server architecture can be complex, requiring specialized skills and knowledge in server administration, network management, and security.
Suitable Scenarios
Client-server architecture is a suitable choice for a wide range of applications, including:
- Web Applications: Websites, web services, and web-based applications often leverage client-server architecture. Clients (web browsers) interact with servers to request and display web pages and data.
- Database Management Systems: Client-server architectures are widely used in database management systems. Clients connect to a central database server to access, manipulate, and store data.
- Email Servers: Email clients interact with email servers to send, receive, and manage emails. Client-server architecture provides a robust and scalable solution for email communication.
- File Sharing: File servers allow users to share files and documents across a network. Clients can access and manage files stored on the server.
Alternative Architectures
While client-server architecture is prevalent, alternative architectures may be more suitable in certain scenarios:
- Peer-to-Peer (P2P): In P2P networks, all devices act as both clients and servers, directly communicating with each other. This architecture is suitable for applications where centralized control is not necessary, such as file sharing and video conferencing.
- Cloud-Based Architecture: Cloud-based architectures utilize remote servers and resources provided by cloud providers. This offers scalability, flexibility, and cost-effectiveness, making it suitable for applications with high traffic and dynamic needs.
- Microservices Architecture: Microservices architecture breaks down applications into small, independent services that communicate with each other. This promotes modularity, scalability, and resilience, making it suitable for complex applications.
Trade-offs
Choosing a client-server architecture involves several trade-offs:
- Centralized Control vs. Decentralization: Client-server architecture provides centralized control over data and resources, but it can also create a single point of failure. P2P networks offer decentralization but can be challenging to manage and secure.
- Scalability vs. Complexity: Client-server architectures can be easily scaled but require complex infrastructure and administration. Cloud-based architectures offer scalability and flexibility but rely on third-party providers.
- Security vs. Accessibility: Centralized security measures can be implemented in client-server architectures, but they can also restrict accessibility. P2P networks offer decentralized security but can be more vulnerable to attacks.
Ending Remarks
Client-server architecture remains a cornerstone of modern technology, providing a robust framework for diverse applications. Understanding its principles empowers developers to build scalable, secure, and efficient systems. As technology evolves, client-server architecture continues to adapt, embracing new trends like cloud computing and mobile-first development. This dynamic duo is poised to shape the future of software development, driving innovation and enhancing user experiences across various domains.
Client-server architecture is a fundamental concept in computing, forming the backbone of many applications we use daily. From streaming services to online games, these systems rely on a collaborative exchange of information. When you’re not working on those projects, perhaps you’d like to take a break and create something fun – check out these cute things to make out of clay.
Returning to the world of client-server, it’s fascinating to see how these seemingly simple interactions enable such complex and interconnected systems.