Servers, the unsung heroes of the digital age, are the powerful machines that underpin our interconnected world. They are the backbone of modern computing, silently processing information, storing data, and delivering services that we rely on every day.
From the websites we browse to the apps we use, servers play a vital role in enabling the digital experiences we take for granted. Understanding servers is essential for anyone who wants to delve deeper into the world of technology and appreciate the complex infrastructure that makes our online lives possible.
Server Architecture
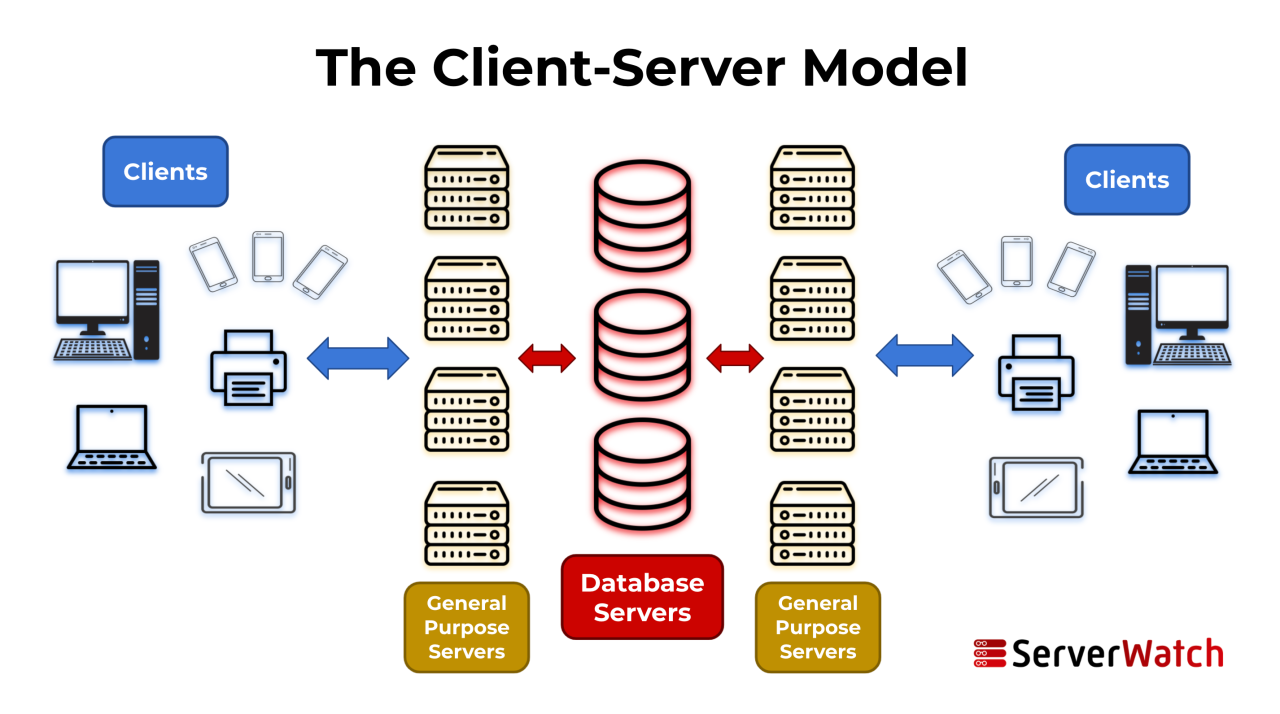
A server is a computer system that provides services to other computers or devices, known as clients. Understanding server architecture is crucial for comprehending how these systems operate and interact. This section delves into the components, architectures, and virtualization concepts associated with servers.
Server Components
Servers are comprised of various components that work together to provide services. These components can be broadly categorized into hardware, operating system, and software.
- Hardware: The physical components of a server include the processor, memory, storage, network interface cards (NICs), and power supply. The processor handles computations, memory stores data temporarily, storage stores data persistently, NICs facilitate network communication, and the power supply provides electricity.
- Operating System: The operating system (OS) acts as the intermediary between the hardware and software applications. It manages resources, provides a user interface, and enables communication between different components. Common server operating systems include Linux, Windows Server, and macOS Server.
- Software: Server software refers to applications that run on the server and provide specific services. These applications can include web servers (Apache, Nginx), database servers (MySQL, PostgreSQL), email servers (Postfix, Sendmail), and application servers (Java EE, .NET).
Server Architectures
Server architectures describe the way servers are organized and interact with clients. Two primary architectures are client-server and peer-to-peer.
- Client-Server Architecture: In this architecture, a dedicated server provides services to multiple clients. Clients request services from the server, and the server responds accordingly. This model is prevalent in web applications, where web servers host websites and respond to requests from web browsers.
- Peer-to-Peer Architecture: In a peer-to-peer architecture, each computer acts as both a client and a server. Computers directly communicate with each other without relying on a central server. Examples include file-sharing networks and online gaming platforms.
Virtualization
Virtualization allows multiple operating systems or applications to run concurrently on a single physical server. This technology enables resource optimization and flexibility.
- Types of Virtualization:
- Operating System Virtualization: Multiple operating systems run independently on a single physical machine, each with its own virtualized hardware resources.
- Application Virtualization: Applications are isolated from the underlying operating system and hardware, enabling portability and simplified deployment.
- Benefits of Virtualization:
- Resource Optimization: Virtualization allows multiple virtual machines to share the resources of a single physical server, reducing hardware costs and energy consumption.
- Flexibility: Virtual machines can be easily created, cloned, and migrated, providing greater flexibility in managing server resources.
- Improved Security: Virtualization can isolate applications and operating systems, enhancing security by preventing malicious software from affecting other virtual machines.
Server Operating Systems
Choosing the right server operating system (OS) is a crucial decision in server architecture. It directly impacts the performance, security, and overall functionality of your server environment. Each OS offers a unique set of features, benefits, and drawbacks, making it essential to carefully evaluate your specific needs and requirements.
Comparison of Popular Server Operating Systems
The three most popular server operating systems are Windows Server, Linux, and macOS Server. Each OS possesses distinct strengths and weaknesses, influencing its suitability for different server applications and environments.
- Windows Server is a robust and feature-rich OS known for its user-friendly interface, extensive software compatibility, and strong support for enterprise applications. It excels in environments where Active Directory, Microsoft Exchange Server, and other Microsoft-specific technologies are essential. However, Windows Server can be more expensive than other options and may require more resources.
- Linux is an open-source OS renowned for its flexibility, security, and cost-effectiveness. It offers a wide range of distributions, each tailored to specific needs, and provides a highly customizable environment. Linux is widely used in web servers, databases, and high-performance computing, making it a popular choice for developers and organizations seeking a stable and secure platform.
- macOS Server is a relatively niche OS designed for Apple environments. It offers seamless integration with Apple devices and services, making it ideal for organizations heavily invested in the Apple ecosystem. However, its limited software compatibility and smaller user base compared to Windows and Linux might hinder its adoption in broader server deployments.
Features and Benefits
- Windows Server offers a comprehensive suite of features, including Active Directory for centralized user management, Hyper-V for virtualization, and support for a vast array of enterprise applications. Its user-friendly interface and extensive documentation make it relatively easy to manage and troubleshoot.
- Linux is known for its open-source nature, providing flexibility and customization options. It offers a wide range of distributions, each with its own set of features and strengths. Linux is also highly secure, with a large community constantly working to identify and address vulnerabilities.
- macOS Server provides a seamless integration with Apple devices and services, making it ideal for organizations using Apple products. It offers features like Time Machine backups, file sharing, and web server capabilities, tailored for the Apple ecosystem.
Security Considerations
- Windows Server has historically been more susceptible to security vulnerabilities compared to Linux. However, Microsoft has significantly improved its security posture in recent years. Regular updates and security patches are crucial for maintaining a secure Windows Server environment.
- Linux is known for its strong security features, including a robust open-source community actively working to identify and address vulnerabilities. Its security-focused design and extensive security tools make it a preferred choice for organizations prioritizing security.
- macOS Server benefits from Apple’s overall focus on security. It offers features like FileVault encryption and Gatekeeper, enhancing its security capabilities. However, its smaller user base might lead to fewer security researchers focusing on its vulnerabilities.
Performance and Scalability, Server
- Windows Server can handle demanding workloads and scale effectively, especially with its virtualization capabilities. However, its resource consumption can be higher compared to Linux, especially in environments with limited resources.
- Linux is renowned for its efficiency and scalability, often requiring fewer resources compared to Windows Server. It excels in handling high-performance workloads and can be scaled to accommodate massive amounts of data and users.
- macOS Server offers a smooth and responsive experience for Apple users, but its scalability might be limited compared to Windows and Linux, especially in large-scale deployments.
Cost Considerations
- Windows Server is generally more expensive than Linux, with licensing fees for each server instance. However, its extensive features and support might justify the higher cost for certain organizations.
- Linux is typically free to use, with a wide range of free and open-source distributions available. Its cost-effectiveness makes it an attractive option for organizations with budget constraints.
- macOS Server is priced competitively with Windows Server, but its limited software compatibility and smaller user base might lead to higher maintenance costs.
Server Management

Server management is the process of overseeing and maintaining the smooth operation of servers, ensuring they are reliable, secure, and perform optimally. This includes a wide range of tasks, from initial setup and configuration to ongoing monitoring, troubleshooting, and updates. Effective server management is crucial for any organization that relies on servers for critical business operations.
Server Administration and Maintenance
Server administration involves a set of tasks that ensure the smooth functioning of servers. This includes:
- Installation and Configuration: This involves setting up the server hardware and software, including the operating system, applications, and network configuration. This step is crucial for establishing the foundation of a functional server environment.
- Security Management: This includes implementing security measures like firewalls, intrusion detection systems, and regular security updates to protect the server and its data from unauthorized access and cyber threats. Strong security practices are essential to maintain the integrity and confidentiality of sensitive information.
- Performance Monitoring: This involves keeping a close eye on server performance metrics like CPU usage, memory utilization, disk space, and network traffic. By analyzing these metrics, administrators can identify potential bottlenecks and optimize server performance for optimal efficiency.
- Troubleshooting and Problem Solving: Server administrators are responsible for diagnosing and resolving server issues, from software glitches to hardware failures. This often involves using logs, monitoring tools, and technical expertise to pinpoint the root cause of problems and implement appropriate solutions.
- Backup and Recovery: Regular backups are crucial to ensure data recovery in case of hardware failures, software errors, or security breaches. Administrators need to implement backup strategies and test the recovery process regularly to ensure data integrity and minimize downtime.
- Software Updates and Patching: Regularly updating software and patching vulnerabilities is essential to protect servers from security threats and ensure compatibility with new technologies. Administrators need to manage updates and patching schedules to minimize downtime and maintain system stability.
- Capacity Planning: As an organization grows, server capacity needs to be adjusted accordingly. Administrators are responsible for forecasting future server needs, scaling resources, and ensuring the server infrastructure can handle increasing workloads without performance degradation.
Monitoring Server Performance and Resource Utilization
Monitoring server performance is essential for identifying potential issues and optimizing server efficiency. By continuously tracking key metrics, administrators can gain insights into server health, resource utilization, and overall performance.
- CPU Usage: Monitoring CPU usage helps identify CPU-intensive processes or potential bottlenecks that may be impacting overall performance. High CPU utilization can indicate a need for additional processing power or optimization of resource-intensive applications.
- Memory Utilization: Keeping track of memory usage allows administrators to identify potential memory leaks or applications consuming excessive memory. Low memory availability can lead to performance degradation and system instability.
- Disk Space: Monitoring disk space helps prevent disk full situations, which can disrupt server operations. Regular disk space monitoring allows for timely action to free up space or expand storage capacity.
- Network Traffic: Tracking network traffic patterns helps identify bandwidth bottlenecks, potential security threats, or unexpected traffic spikes. Understanding network usage patterns is crucial for optimizing network performance and ensuring reliable connectivity.
- System Logs: Analyzing system logs provides valuable insights into server events, errors, and security incidents. By reviewing logs regularly, administrators can identify potential issues early on and take proactive measures to address them.
Server Management Tools and Techniques
Various tools and techniques are available to assist server administrators in managing and maintaining servers effectively.
- Monitoring Tools: These tools provide real-time insights into server performance metrics, resource utilization, and system events. Popular monitoring tools include Nagios, Zabbix, and Prometheus, offering features like automated alerts, customizable dashboards, and historical data analysis.
- Configuration Management Tools: These tools help automate server configuration tasks, ensuring consistency and reducing manual errors. Tools like Puppet, Chef, and Ansible allow administrators to define server configurations and deploy them across multiple servers with ease.
- Virtualization Platforms: Virtualization technologies like VMware, Hyper-V, and KVM allow administrators to create and manage virtual machines, consolidating multiple servers onto a single physical machine. This improves resource utilization, reduces hardware costs, and simplifies server management.
- Cloud Computing Platforms: Cloud platforms like AWS, Azure, and Google Cloud provide infrastructure as a service (IaaS), allowing organizations to access computing resources on demand. Cloud platforms offer scalability, flexibility, and pay-as-you-go pricing models, simplifying server management and reducing infrastructure costs.
- Scripting and Automation: Automating repetitive tasks through scripting languages like Python, Bash, or PowerShell can significantly improve server management efficiency. Automation helps reduce manual errors, streamline processes, and free up administrators’ time for more strategic tasks.
Server Security
Server security is paramount in today’s digital landscape, as servers store and process sensitive data that can be vulnerable to various threats. Implementing robust security measures is essential to protect your server infrastructure and the data it houses.
Common Security Threats to Servers
Servers are susceptible to various security threats, including:
- Malware: Malicious software designed to infiltrate and damage servers, steal data, or disrupt operations. This includes viruses, worms, Trojans, and ransomware.
- Denial-of-service (DoS) attacks: Attempts to overwhelm a server with traffic, rendering it inaccessible to legitimate users.
- Unauthorized access: Gaining access to a server without proper authorization, often through stolen credentials or exploiting vulnerabilities.
- Data breaches: Unauthorized access to sensitive data stored on a server, leading to data theft, misuse, or compromise.
- Misconfigurations: Incorrect settings or configurations that create security loopholes, making the server vulnerable to attacks.
- Zero-day exploits: Attacks exploiting newly discovered vulnerabilities before security patches are available.
- Social engineering: Manipulating individuals into granting access or revealing sensitive information.
Best Practices for Securing Servers
To mitigate security threats, implement the following best practices:
- Firewalls: Act as a barrier between the server and the external network, blocking unauthorized access and malicious traffic.
- Intrusion detection systems (IDS): Monitor network traffic for suspicious activity and alert administrators of potential threats.
- Encryption: Protect data in transit and at rest by converting it into an unreadable format, making it inaccessible to unauthorized individuals.
- Strong passwords and multi-factor authentication (MFA): Utilize strong passwords and MFA to prevent unauthorized access to accounts.
- Regular security audits: Periodically assess the server’s security posture to identify vulnerabilities and implement necessary safeguards.
- Patch management: Apply security patches and updates promptly to address vulnerabilities and improve the server’s security.
- Secure configuration management: Ensure all server configurations are secure and follow best practices.
- Regular backups: Create regular backups of critical data to recover from data loss caused by security incidents.
- Employee training: Educate employees about security threats and best practices to minimize the risk of human error.
Security Vulnerabilities and Mitigation Strategies
Here are some common security vulnerabilities and their mitigation strategies:
Common Vulnerabilities and Mitigation Strategies
- SQL injection: Exploiting vulnerabilities in web applications to manipulate database queries, potentially leading to data theft or manipulation.
- Mitigation: Implement input validation, parameterized queries, and secure coding practices to prevent SQL injection attacks.
- Cross-site scripting (XSS): Injecting malicious scripts into websites or web applications to steal user data or hijack sessions.
- Mitigation: Use input sanitization, output encoding, and content security policies to prevent XSS attacks.
- Remote code execution (RCE): Exploiting vulnerabilities to execute arbitrary code on a server, potentially giving attackers full control.
- Mitigation: Keep software up to date, apply security patches, and use secure coding practices to prevent RCE attacks.
- Buffer overflow: Overwriting memory buffers with malicious data, potentially allowing attackers to execute code or gain control of the system.
- Mitigation: Use secure programming languages, employ boundary checks, and implement stack protection mechanisms to prevent buffer overflow attacks.
- Denial-of-service (DoS) attacks: Overwhelming a server with traffic, making it unavailable to legitimate users.
- Mitigation: Use firewalls, rate limiting, and load balancing to mitigate DoS attacks.
Server Applications
Servers are the backbone of modern computing, providing the infrastructure for countless services and applications. They act as central hubs, storing and processing data, delivering content, and enabling communication across networks. Understanding the diverse applications of servers is crucial for comprehending their role in our digital world.
Hosting Websites and Web Applications
Servers are fundamental for hosting websites and web applications. They act as the central point where website files are stored and made accessible to users worldwide. When a user enters a website address in their browser, a request is sent to the server hosting the website. The server then retrieves the requested files, including HTML, CSS, JavaScript, and images, and sends them back to the user’s browser for rendering.
Cloud Computing and Data Storage
Servers are essential for cloud computing, which involves delivering computing services – including servers, storage, databases, networking, software, analytics, and intelligence – over the internet. Cloud providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) leverage vast server farms to offer a wide range of services to businesses and individuals. These servers are responsible for storing, processing, and managing data, allowing users to access and utilize resources on demand.
Examples of Server Applications
Servers are used in a wide range of applications, including:
- Web Servers: Apache, Nginx, and Microsoft IIS are popular web server software that handle requests from web browsers, deliver web pages, and manage website content.
- Database Servers: MySQL, PostgreSQL, and Oracle Database are examples of database servers that store, manage, and retrieve data for applications. They ensure data integrity, security, and efficient access.
- Email Servers: Sendmail, Postfix, and Exchange Server are used to send, receive, and manage emails. They handle email routing, spam filtering, and message storage.
- File Servers: Samba, NFS, and FTP servers are used for sharing files across networks. They provide centralized storage and access to files for multiple users.
- Game Servers: Dedicated servers are used to host online games, providing a stable and secure environment for multiplayer gaming experiences.
- Application Servers: JBoss, WebSphere, and Tomcat are examples of application servers that run and manage web applications. They provide a platform for deploying, executing, and managing web applications.
Server Deployment

Server deployment is the process of installing, configuring, and making a server accessible for use. It involves a series of steps that ensure the server is ready to handle its intended workload and is accessible to users.
Deployment Models
Server deployment models define the physical location and management of the server infrastructure. The choice of deployment model depends on various factors, including budget, security requirements, and scalability needs.
- On-premises Deployment: In this model, servers are physically located within an organization’s own data center. This provides greater control over the infrastructure, but requires significant upfront investment in hardware, software, and maintenance.
- Cloud-based Deployment: Cloud providers offer virtualized server infrastructure that can be accessed and managed remotely. This model offers scalability, flexibility, and cost-effectiveness, as organizations pay only for the resources they use. Popular cloud providers include Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
Factors to Consider When Choosing a Deployment Method
Choosing the right deployment method is crucial for ensuring the server meets the organization’s needs. Key factors to consider include:
- Cost: On-premises deployment requires significant upfront investment in hardware and software, while cloud-based deployment offers a pay-as-you-go model. Organizations need to carefully analyze their budget and long-term cost implications.
- Scalability: Cloud-based deployment offers high scalability, allowing organizations to easily adjust their server resources based on demand. On-premises deployment may require more planning and investment to scale infrastructure.
- Security: Both on-premises and cloud-based deployment have their own security considerations. On-premises deployment provides greater control over security measures, while cloud providers offer robust security features and compliance certifications.
- Management: Cloud-based deployment simplifies server management, as providers handle infrastructure maintenance and updates. On-premises deployment requires dedicated IT staff for management and maintenance.
- Flexibility: Cloud-based deployment offers greater flexibility, allowing organizations to quickly deploy new servers and applications. On-premises deployment requires more planning and lead time for infrastructure changes.
Server Optimization
Server optimization is a crucial aspect of server management, aiming to enhance server performance, resource utilization, and overall efficiency. By optimizing server resources, administrators can ensure smooth operation, prevent performance bottlenecks, and deliver optimal user experiences.
Performance Tuning Strategies
Performance tuning strategies involve identifying and addressing performance bottlenecks, fine-tuning server configurations, and implementing best practices to enhance server performance. These strategies can significantly improve server responsiveness, reduce latency, and enhance overall user experience.
- Hardware Optimization: This involves selecting the appropriate hardware components for the server’s workload, ensuring sufficient RAM, CPU power, and storage capacity. Regular hardware maintenance and upgrades can also contribute to optimal performance.
- Software Optimization: Software optimization focuses on fine-tuning server configurations, including operating system settings, database parameters, and application configurations. Regular software updates and patches are essential for security and performance.
- Code Optimization: Optimizing code involves streamlining application logic, reducing resource consumption, and minimizing database queries. This can significantly improve application performance and server efficiency.
- Caching: Caching frequently accessed data in memory can reduce the need for repeated database queries, leading to faster response times and improved performance. This is especially beneficial for dynamic websites and applications.
- Load Balancing: Load balancing distributes incoming traffic across multiple servers, preventing any single server from becoming overloaded. This ensures even resource utilization and maintains optimal performance under high traffic conditions.
Load Balancing
Load balancing is a technique used to distribute incoming traffic across multiple servers, ensuring that no single server becomes overloaded. It is a critical aspect of server optimization, especially for websites and applications experiencing high traffic volumes.
- Round Robin: This method distributes traffic to servers in a sequential manner, ensuring that each server receives an equal share of the workload. This is a simple and effective method for load balancing, particularly for small-scale deployments.
- Least Connections: This approach directs traffic to the server with the fewest active connections, ensuring that servers with more capacity handle the incoming traffic. This is a useful method for optimizing server resource utilization and minimizing response times.
- Weighted Round Robin: This method assigns weights to each server, indicating its capacity and processing power. Traffic is distributed proportionally to the weights, ensuring that servers with higher capacity handle more requests. This is a flexible approach that allows for efficient resource allocation based on server capabilities.
- IP Hashing: This method uses the client’s IP address to determine the server that will handle the request. This ensures that requests from the same client are always directed to the same server, which can be beneficial for maintaining session state and improving performance for applications that rely on persistent connections.
Server Trends and Future Directions
The server landscape is constantly evolving, driven by technological advancements and changing user demands. Emerging technologies, such as edge computing and serverless computing, are reshaping the way servers are designed, deployed, and utilized. Meanwhile, the rise of cloud computing has significantly impacted the traditional server market, leading to new models of server ownership and consumption. This section explores these trends and examines future directions in server technology and its applications.
Edge Computing
Edge computing brings processing power closer to the source of data, reducing latency and improving responsiveness. It is particularly beneficial for applications requiring real-time data processing, such as streaming services, gaming, and autonomous vehicles. Edge computing involves deploying servers at the network edge, closer to end-users. This distributed approach allows for faster data processing and reduces reliance on centralized data centers.
- Reduced Latency: By processing data closer to users, edge computing minimizes the time it takes for requests to be processed and responses to be delivered. This is crucial for applications requiring low latency, such as online gaming and video conferencing.
- Improved Responsiveness: Edge computing enables faster response times and improved user experience, especially in areas with limited network connectivity.
- Increased Bandwidth Efficiency: By processing data locally, edge computing reduces the amount of data that needs to be transmitted over the network, leading to improved bandwidth efficiency.
- Enhanced Security: Edge computing can improve security by keeping sensitive data closer to users and reducing the risk of data breaches during transmission.
Serverless Computing
Serverless computing allows developers to run code without managing servers. This eliminates the need for server provisioning, scaling, and maintenance, enabling developers to focus on application logic. Serverless platforms handle the underlying infrastructure, automatically scaling resources based on demand.
- Reduced Operational Overhead: Serverless computing frees developers from managing server infrastructure, allowing them to focus on building applications.
- Scalability and Elasticity: Serverless platforms automatically scale resources based on demand, ensuring optimal performance and cost efficiency.
- Pay-as-you-go Pricing: Serverless computing is typically priced based on usage, allowing developers to pay only for the resources they consume.
- Faster Deployment: Serverless applications can be deployed quickly and easily, reducing development time and accelerating time-to-market.
Impact of Cloud Computing
Cloud computing has revolutionized the server market by providing on-demand access to computing resources over the internet. This has led to a shift from traditional on-premises server deployments to cloud-based solutions.
- Increased Flexibility and Scalability: Cloud computing offers greater flexibility and scalability compared to on-premises servers. Businesses can easily scale their resources up or down based on their needs.
- Reduced Costs: Cloud computing can significantly reduce upfront costs associated with server hardware and maintenance.
- Enhanced Security and Reliability: Cloud providers offer robust security measures and high levels of reliability, ensuring data protection and uptime.
- Innovation and Agility: Cloud computing enables businesses to adopt new technologies and innovate faster, as they have access to a wide range of services and tools.
Future Trends in Server Technology
Server technology continues to evolve rapidly, driven by advancements in hardware, software, and network infrastructure. Future trends include:
- Increased Processing Power: Server processors are expected to become even more powerful, enabling faster data processing and improved performance.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are becoming increasingly important in server applications, enabling intelligent automation and data analysis.
- Quantum Computing: Quantum computing has the potential to revolutionize server technology by enabling faster and more efficient computations.
- Internet of Things (IoT): The proliferation of IoT devices is driving demand for servers that can handle large volumes of data and support connected devices.
Final Thoughts
As technology continues to evolve, servers will continue to play a crucial role in shaping the future of computing. From the rise of cloud computing to the emergence of new technologies like edge computing and serverless computing, servers are at the forefront of innovation, driving progress and expanding the boundaries of what’s possible in the digital realm.
Just like a server needs a solid foundation to run smoothly, building a house requires a thorough plan. You wouldn’t start building a house without a blueprint, would you? Similarly, understanding the architecture and configuration of a server is crucial before you start deploying applications.
For a detailed guide on building a house step by step, check out this helpful resource: building a house step by step. Back to servers, once you’ve got the basics down, you can move on to more complex tasks like managing databases and ensuring security.




